Secure Your Kubernetes Containers at the Speed of CI/CD
Leave no cluster or container behind. Achieve end-to-end protection from build to runtime.

Why Choose Our Kubernetes Security Solution?
Protect Your Containers, Power Your Business.
Designed for Containers
Unlike host-centric EDR, our tools understand Kubernetes orchestration and container isolation
Real-Time Threat Detection
Identify and stop malicious activity, from crypto-mining malware to reverse shells in your cloud workloads
Automated Response
Drastically reduce Mean Time to Respond (MTTR) with automated containment actions like pod isolation and process termination
Kubernetes-Native Deployment
Integrate seamlessly into your environment with easy Helm chart deployment
Streamlined Compliance & Governance
Automatically enforce security policies and demonstrate compliance with standards like CIS Benchmarks without manual intervention
Advanced Security Isolation & Zero-Trust Enforcement
Enforce granular security policies to isolate compromised workloads and prevent lateral movement, containing breaches before they spread
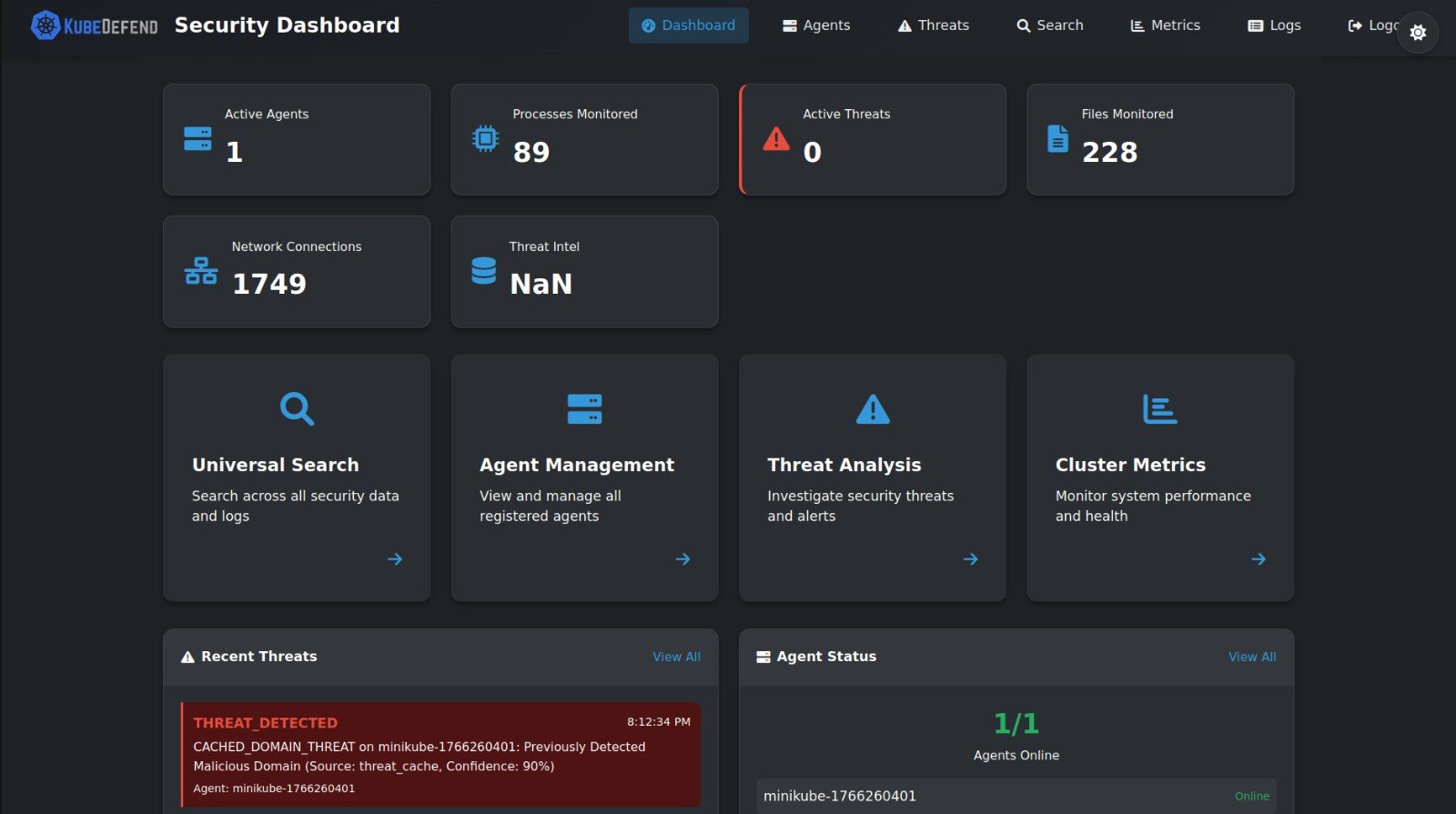
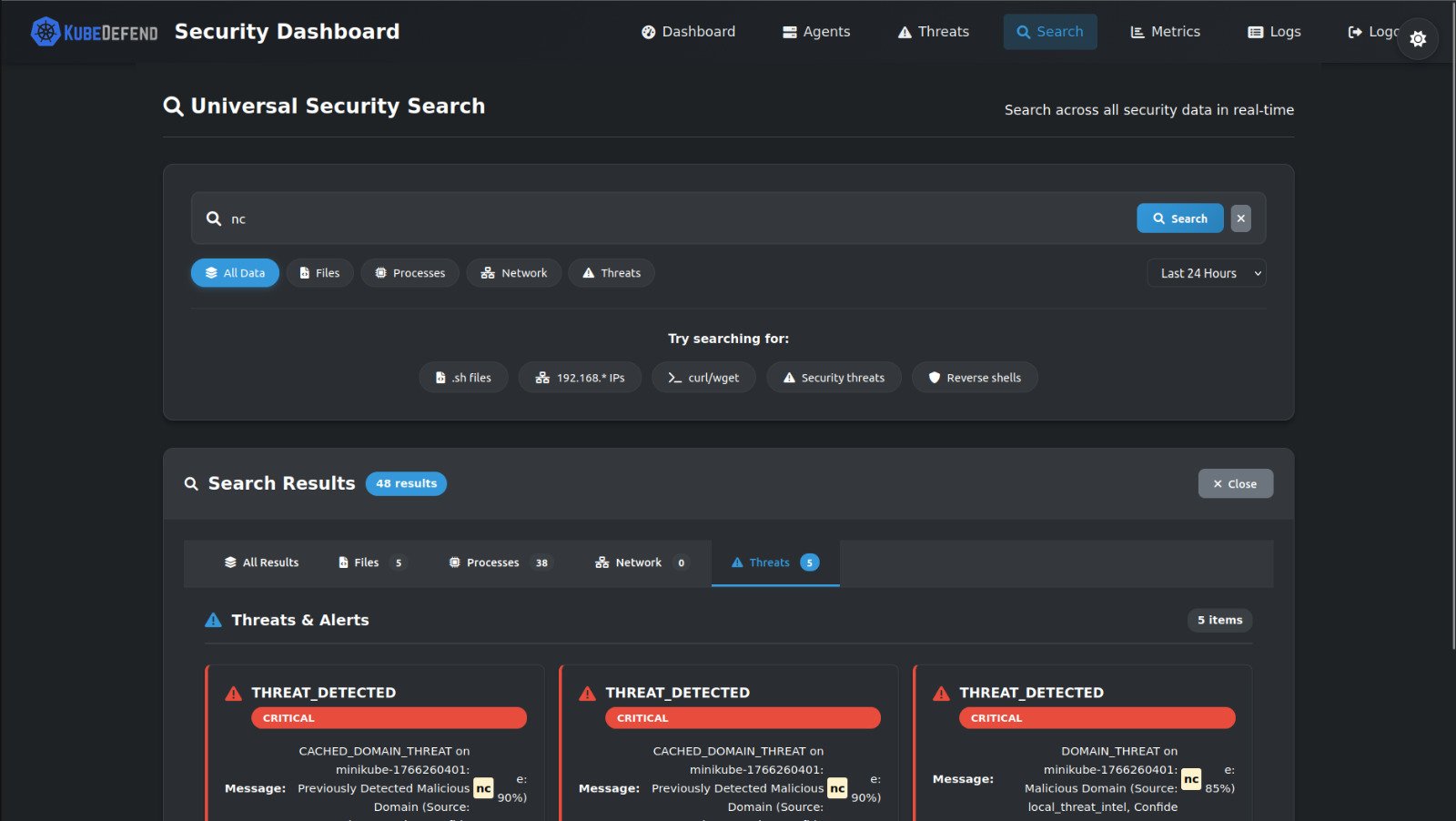
How KubeDefend Secures Your Cluster
Kubedefend provides a lightweight, powerful security agent that integrates directly into your Kubernetes environment, delivering real-time threat detection and automated response from deployment to runtime.
Deploy the Kubedefend Agent
Seamless Integration in Minutes
Get started in under five minutes with a single Helm command. Our Kubernetes-native agent deploys as a DaemonSet, ensuring every node in your cluster is instantly protected without disrupting your existing workloads.
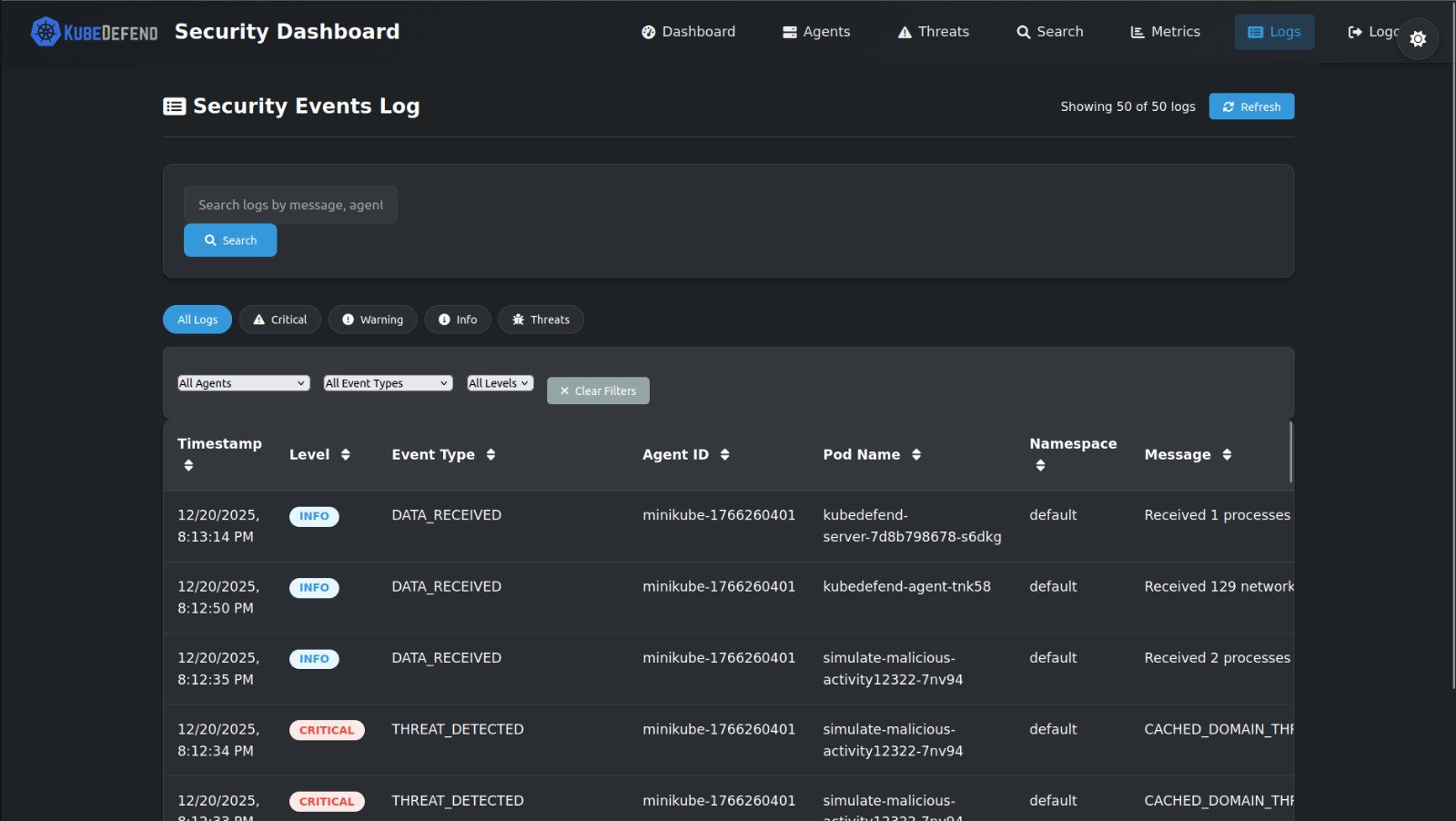
Continuous Monitoring & Data Collection
Deep Visibility into Container Activity
The agent immediately begins collecting rich telemetry from across your cluster. This includes process execution, file system activity, network connections, and Kubernetes API events—all correlated with pod labels and deployment context for complete security visibility.
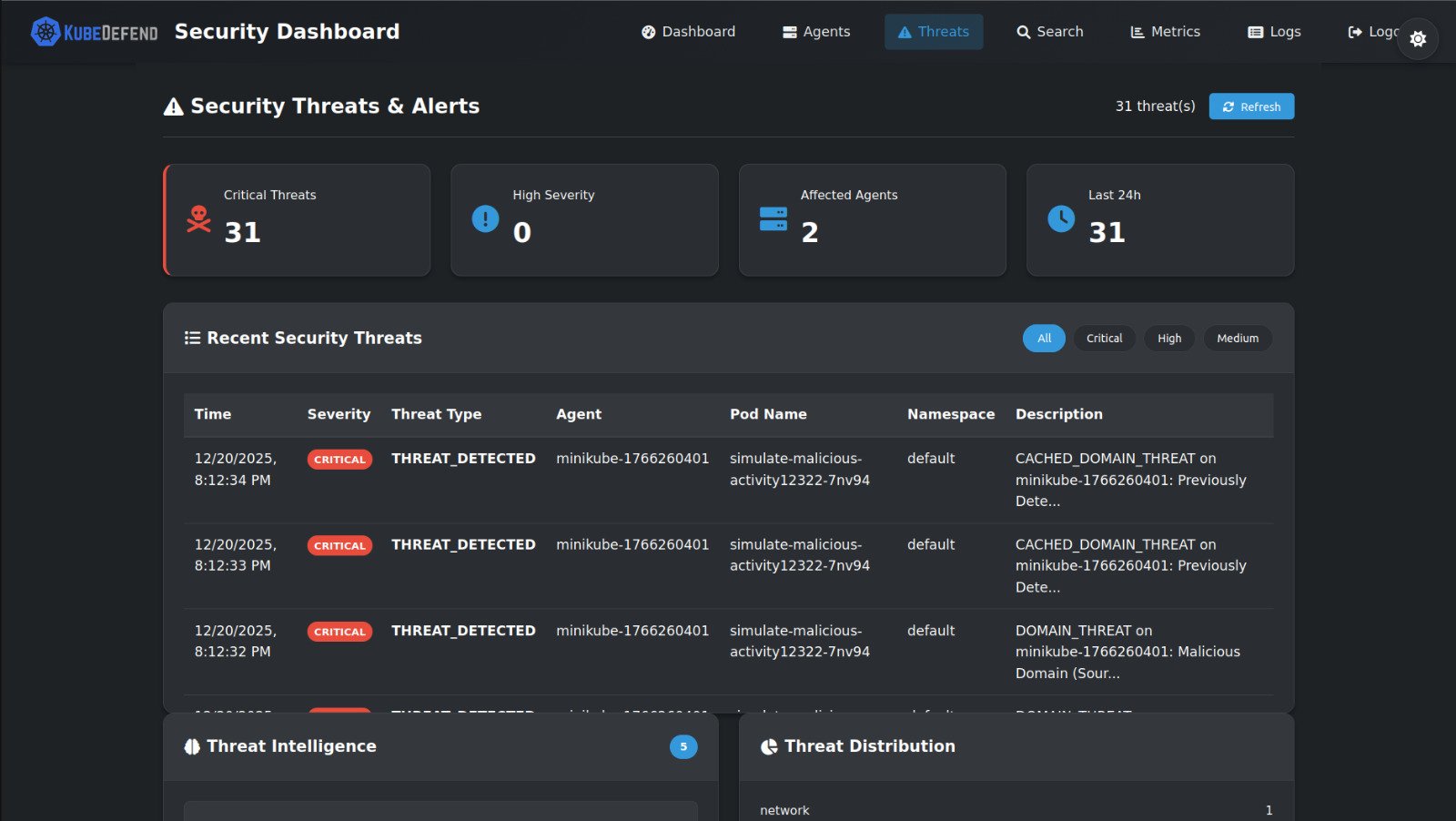
Real-Time Threat Detection & Analysis
Identify Threats Before They Impact Your Business
Our detection engine analyzes the collected data in real-time using YARA rules, behavioral analysis, and threat intelligence. It identifies malicious patterns like crypto-mining activity, suspicious network callbacks, privilege escalation attempts, and compliance violations specific to containerized environments.
Automated Response & Containment
Stop Attacks Instantly, Without Manual Intervention
When a threat is detected, Kubedefend automatically executes containment actions based on your security policies. This includes isolating compromised pods, terminating malicious processes, or blocking network traffic—drastically reducing your mean time to response (MTTR) and limiting potential damage.
KubeDefend Technical Specifications
Enterprise-grade Kubernetes security with minimal performance overhead.
Designed for production workloads with zero single-point-of-failure architecture. Each agent operates independently while coordinating through the central kubedefend-server for unified policy enforcement.
Our detection engine processes security events with sub-second latency, analyzing process activity, network connections, and file system changes across your entire cluster. The engine correlates events with Kubernetes context for accurate, actionable alerts.
Cluster Security, Simplified
Straightforward plans based on your security requirements.
Free Plan
$
0
/ forever
1 Pod Support
1 Node Support
Limited speed
Limited information gathering
Pro Plan
$
99.99
/ per month
10 Pods Support
3 Node Support
Unlimited speed
Limited information gathering
Premium Plan
$
199.99
/ per month
Unlimited Pods Support
Unlimited Node Support
Unlimited speed
Unlimited information gathering
Secure Your Cluster Today
Stop leaving your Kubernetes environment exposed. Deploy Kubedefend and achieve enterprise-grade runtime protection in minutes.